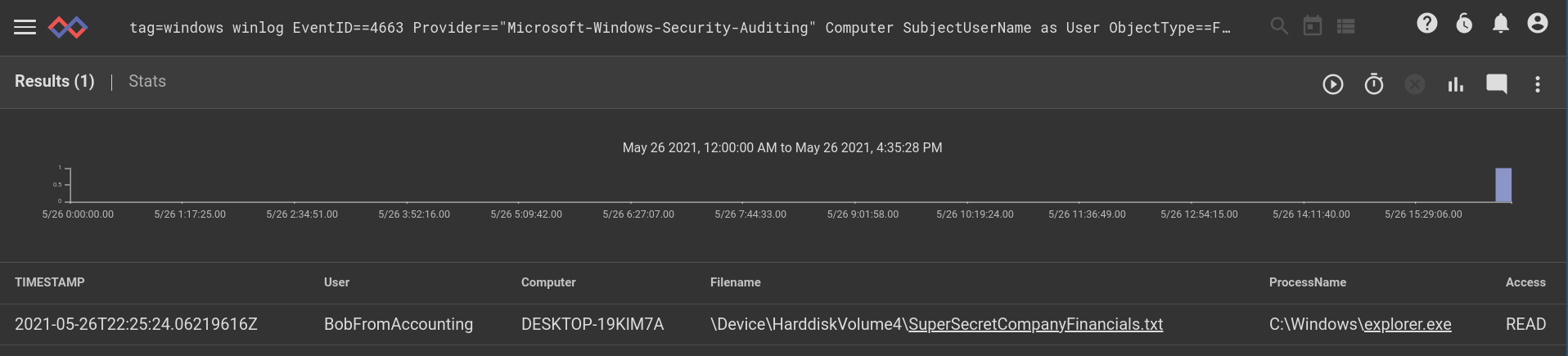
For this week we are going to look at external storage auditing in Windows. This query shows a nice succinct table of file activity on external storage, which is a great way to monitor external storage activity. Whether it is BobFromAccounting moving important data onto external storage devices or firing off executable code from USB keys, external storage auditing is critical in many environments. We will use some eval hackery to turn the AccessMask (a bit mask) into a human readable word.
The Query
tag=windows winlog EventID==4663 Provider=="Microsoft-Windows-Security-Auditing" ObjectType==File ProcessName AccessMask Computer SubjectUserName as User ObjectName as Filename
| eval if ((toInt(AccessMask) & 0x2) != 0) {
setEnum("Access", "WRITE")
} else if ((toInt(AccessMask) & 0x4) != 0) {
setEnum("Access", "READ")
}
| table TIMESTAMP User Computer Filename ProcessName Access
An example Entry
<Event xmlns='http://schemas.microsoft.com/win/2004/08/events/event'><System><Provider Name="Microsoft-Windows-Security-Auditing" Guid="{54849625-5478-4994-A5BA-3E3B0328C30D}" /><EventID>4663</EventID><Version>1</Version><Level>0</Level><Task>12812</Task><Opcode>0</Opcode><Keywords>0x8020000000000000</Keywords><TimeCreated SystemTime="2021-05-26T12:00:0.634739700Z" /><EventRecordID>8831</EventRecordID><Correlation /><Execution ProcessID="4" ThreadID="4188" /><Channel>Security</Channel><Computer>DESKTOP-19KIM7A</Computer><Security /></System><EventData><Data Name="SubjectUserSid">S-1-5-21-2880652929-2813639029-62145511-1002</Data><Data Name="SubjectUserName">BobFromAccounting</Data><Data Name="SubjectDomainName">DESKTOP-19KIM7A</Data><Data Name="SubjectLogonId">0x18dae1</Data><Data Name="ObjectServer">Security</Data><Data Name="ObjectType">File</Data><Data Name="ObjectName">\Device\HarddiskVolume4\SuperSecretCompanyFinancials.txt</Data><Data Name="HandleId">0x20a0</Data><Data Name="AccessList">%%4418</Data><Data Name="AccessMask">0x4</Data><Data Name="ProcessId">0x458</Data><Data Name="ProcessName">C:\Windows\explorer.exe</Data><Data Name="ResourceAttributes" /></EventData></Event>