Security
Data Platform
Enabling Actionable Insights

Gravwell provides a modern, scalable approach to security data management, enabling security teams to analyze data on demand using a piped query language.
The Gravwell search pipeline’s extensible structure promotes threat hunting and data exploration by using structure-on-read to extract, transform, and visualize data to execute complex and wide-reaching investigations.
choosing an SDP vs SIEM
WHAT IS GRAVWELL?
SIEM Challenges
- Expensive licensing and storage
- Performance degradation with large datasets
- Limited flexibility for deep threat hunting
- High operational overhead for managing out of the box rules that are not customized to the users environment
SDP Challenges
- Requires tuning to your environment
- Can be complex to implement
- Less focus on "out-of-the-box" content
- Need for data engineering expertise
between SDP vs SIEM
SDP KEY FEATURES
Structure on Read
piped Query Language
capabilities for rapid threat
detection.
Scalability
Threat Hunting Enhanced
conduct deeper investigations
without pre-configured rules
Open Data Model
various security tools and sources.
Deployment
air gapped environments.
While SDPs can function independently, they also enhance SIEM capabilities by providing
deeper analysis, improved performance, and cost-effective data retention. Many
organizations use SDPs as a secondary layer of security intelligence to refine
SIEM-generated alerts.
Improve your workflow
.png)
Detect &
Investigate
Effortlessly filter and transform data to identify anomalies and understand user behavior, detecting potential security threats and attacker TTPs.
The Gravwell search pipeline’s extensible structure promotes threat hunting and data exploration by using structure-on-read to extract, transform, and visualize data to execute complex and wide-reaching investigations. Since Gravwell uses one language for all investigations and detections, you can easily convert any threat hunt results directly into scheduled detections.
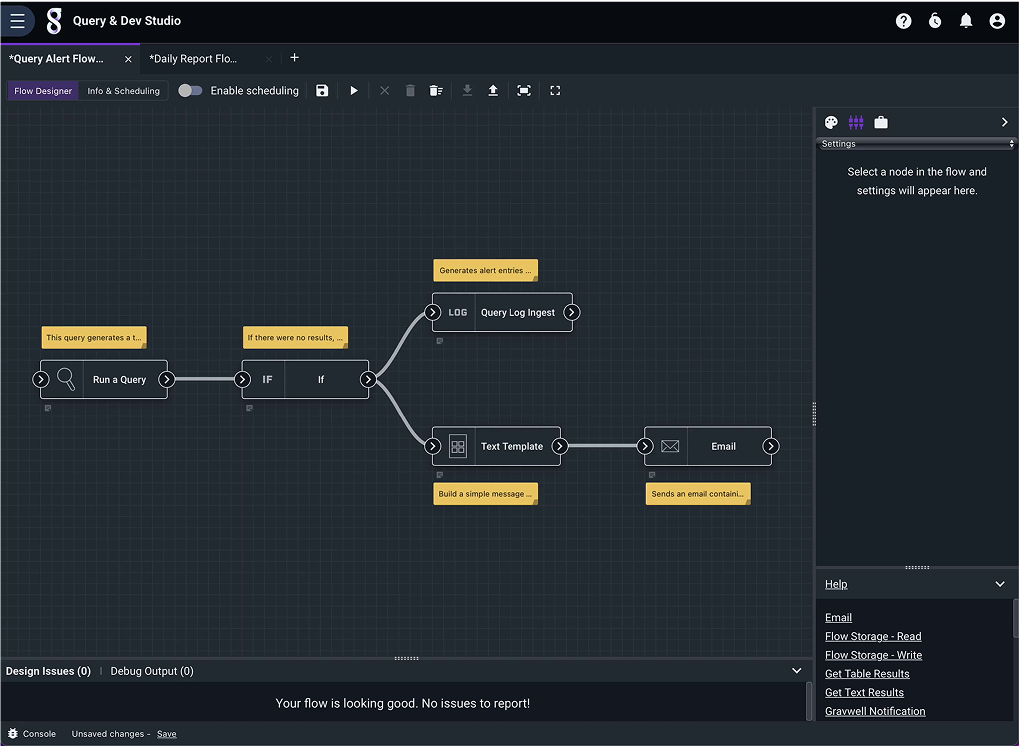
adds dynamic responses to act on detected events.
Respond
Flows extends the reach of analysts and engineers to act on information with notifications, HTTP requests, messages, and more.
Flows can aggregate and summarize data, act as a response to a detected event, conduct secondary searche,s and interact with external systems.
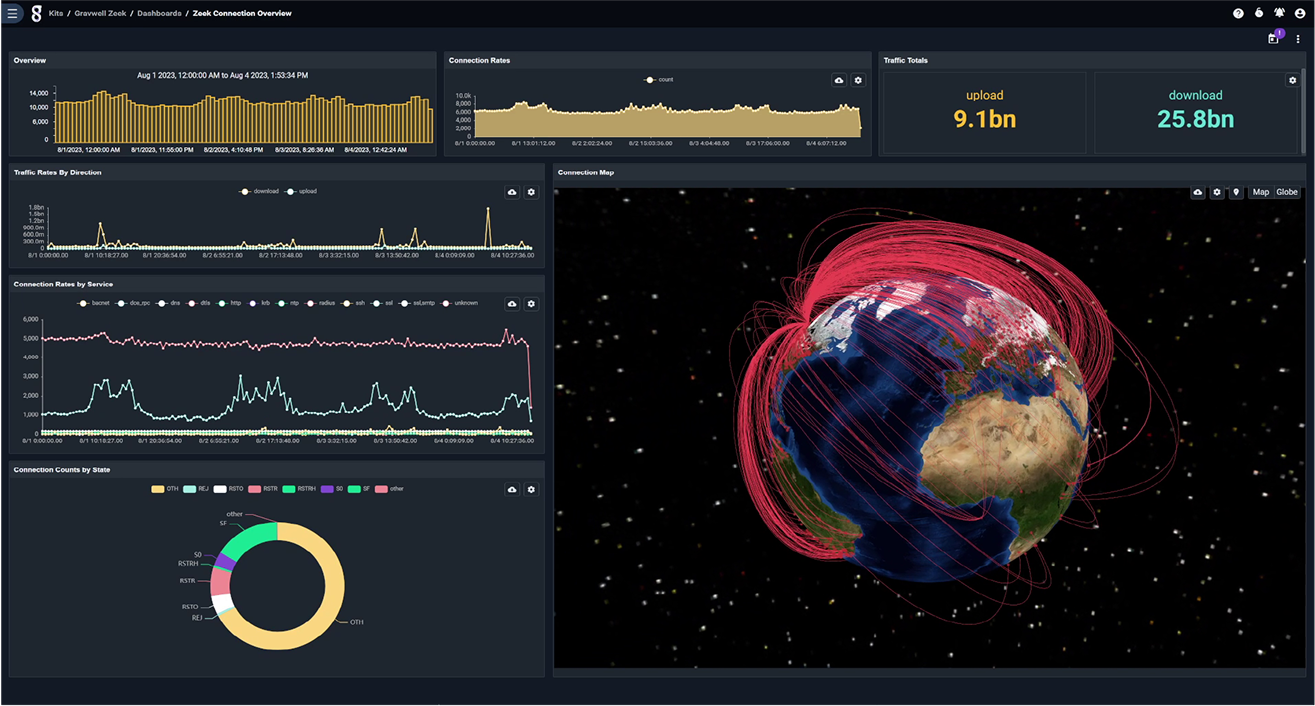
Visualize
Gravwell’s Dashboards
Transform Data Into
Actionable Insights.
Utilizing various charts and graphs, these
visualizations help identify anomalies and
make sense of complex datasets, accelerating response to critical scenarios
Build custom dashboards with Gravwell
Templates for dynamic and intuitive data
interaction. This dashboard-building
experience scales insights across teams,
aiding issue resolution and strategic planning.
Gravwell also provides Kits that come with
pre-built dashboards providing the most
commonly requested visualizations for the
most popular data sources.
See Gravwell
in Action
Searching for no limits and no nonsense?
Contact our team to schedule your demo and leverage Gravwell in
your organization.
DOCUMENTATION
All Gravwell documentation is open to everyone.
If you’re just starting out with Gravwell, we recommend reading the Quick Start first, then moving on to the Search pipeline documentation to learn more.
