Introduction
 This is my boss, Kris, kayaking down a street. He doesn’t think there’s anything wrong with this scene. This picture is also a metaphor for how he interacts with our internal Gravwell deployment and, as a result, nobody trusts him. Fortunately, Gravwell 5.3 now includes Capability Based Access Control (CBAC), which allows us to prevent Kris from cyber-kayaking in places we’d rather him not.
This is my boss, Kris, kayaking down a street. He doesn’t think there’s anything wrong with this scene. This picture is also a metaphor for how he interacts with our internal Gravwell deployment and, as a result, nobody trusts him. Fortunately, Gravwell 5.3 now includes Capability Based Access Control (CBAC), which allows us to prevent Kris from cyber-kayaking in places we’d rather him not.
Let’s walk through an example by restricting Kris, denying him access to resources and to all but one tag in our Gravwell system.
Overview of CBAC
Capability Based Access Control (CBAC) is a system that lets admins assign fine-grained access restrictions to the various Gravwell features, such as search, resources, tokens, etc. Access can be assigned to individual users or to groups. The full list of configurable features can be found in Grawvell’s CBAC documentation.
When using CBAC, users receive access to a feature through explicit “grants” to their specific user, as well as inherited grants from any groups they are a member of.
Additionally, CBAC provides tag access controls to restrict the tags a user can search and ingest into. When using tag restrictions, a user without a given tag grant won’t even be able to see that the tag exists.
Let’s look at how to enable and configure CBAC, using our flailing monkey of a inquisitive boss as an example.
Enabling CBAC
If your Gravwell license supports it, you can enable CBAC by simply adding the following configuration parameter to your Gravwell Webserver configuration (in the global section):
Enable-CBAC=true
CBAC uses a default-deny policy, so on your first use, all non-admin users will have no grants, meaning they won’t be able to interact with the system at all beyond setting their account preferences.
We could stop here, knowing that by simply enabling CBAC, we’ve removed all of Kris’ access to our Gravwell system, but we should probably give him some grants just to avoid causing him to honk like a goose ask questions.
Configuring Users and Groups
Admin users aren’t affected by CBAC policies. After enabling CBAC, login as an admin and head over to the users and groups configuration section. We’ll edit our non-admin user, Kris, and select the “Capabilities” tab, as shown below.
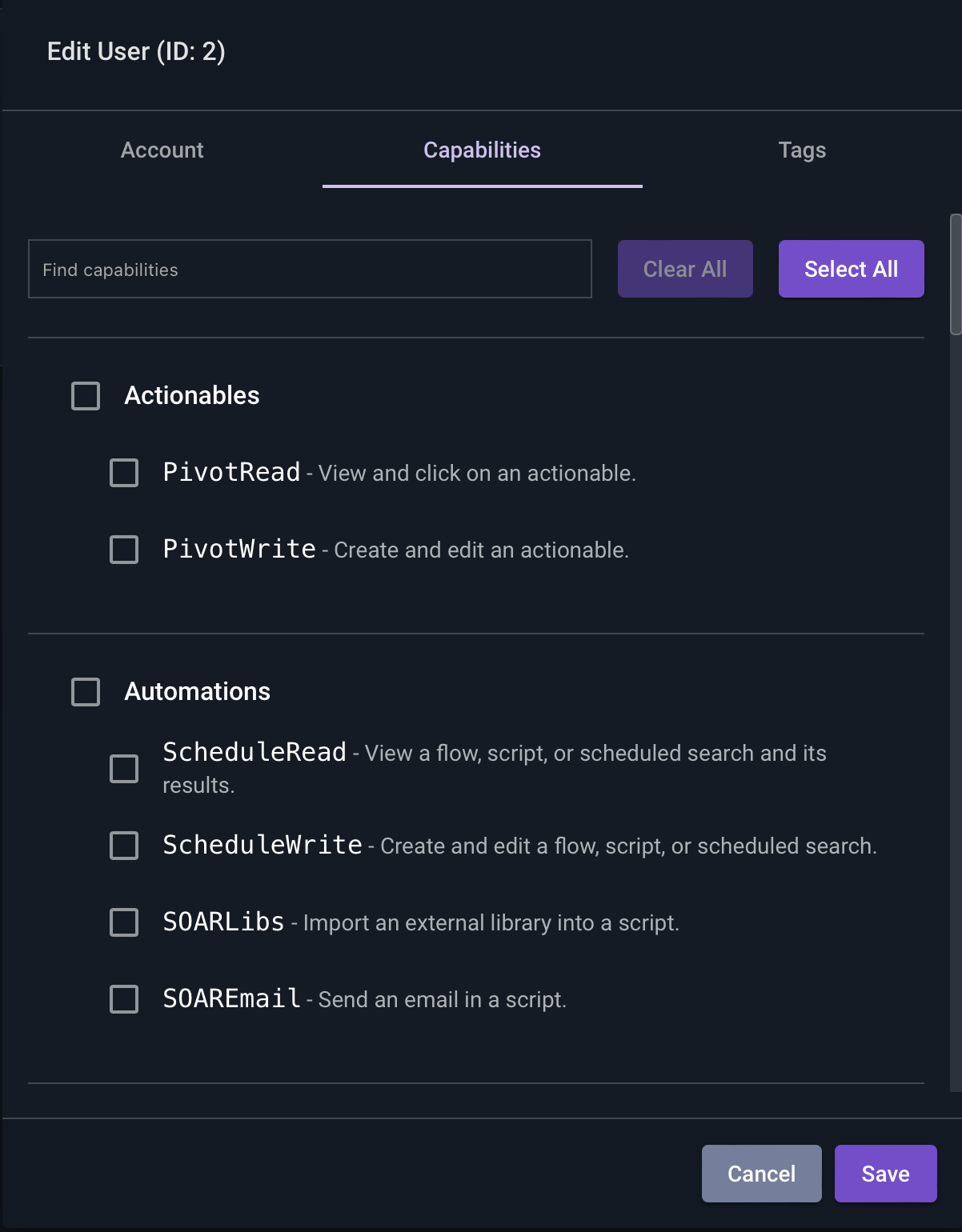
From here we can select any of the features we want Kris to have. Any features left unchecked will be disabled in the GUI. Additionally, any features that can be accessed through search or flows (such as reading resources) will be disabled in those features as well.
Let’s give Kris all features except resources.
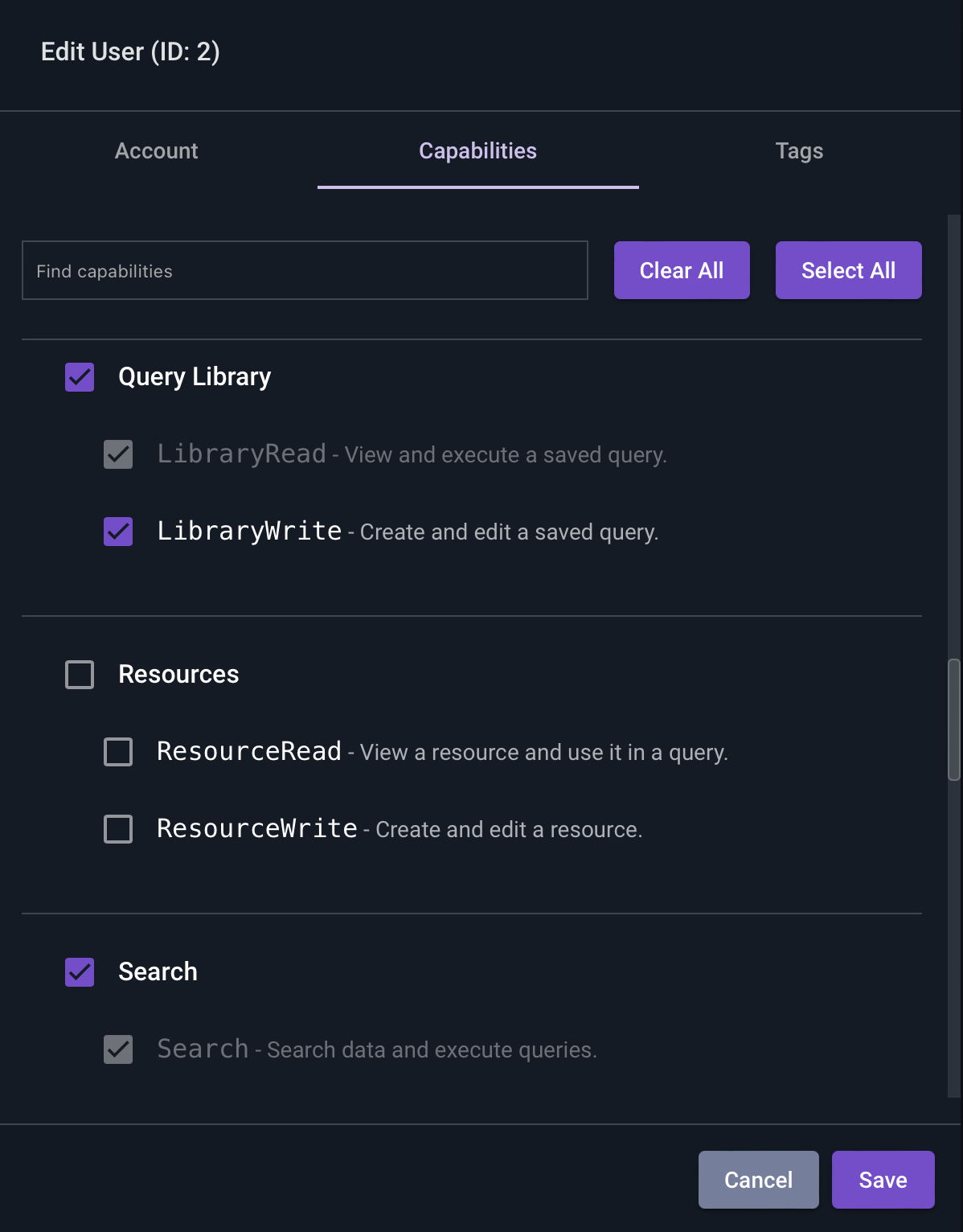
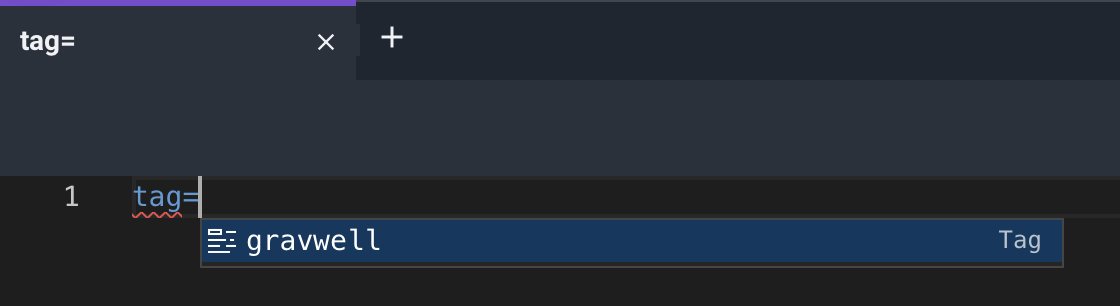
Additionally, let’s restrict Kris’ tag access to just the “gravwell” tag. We’ll select the “Tags” tab, and select “gravwell”.
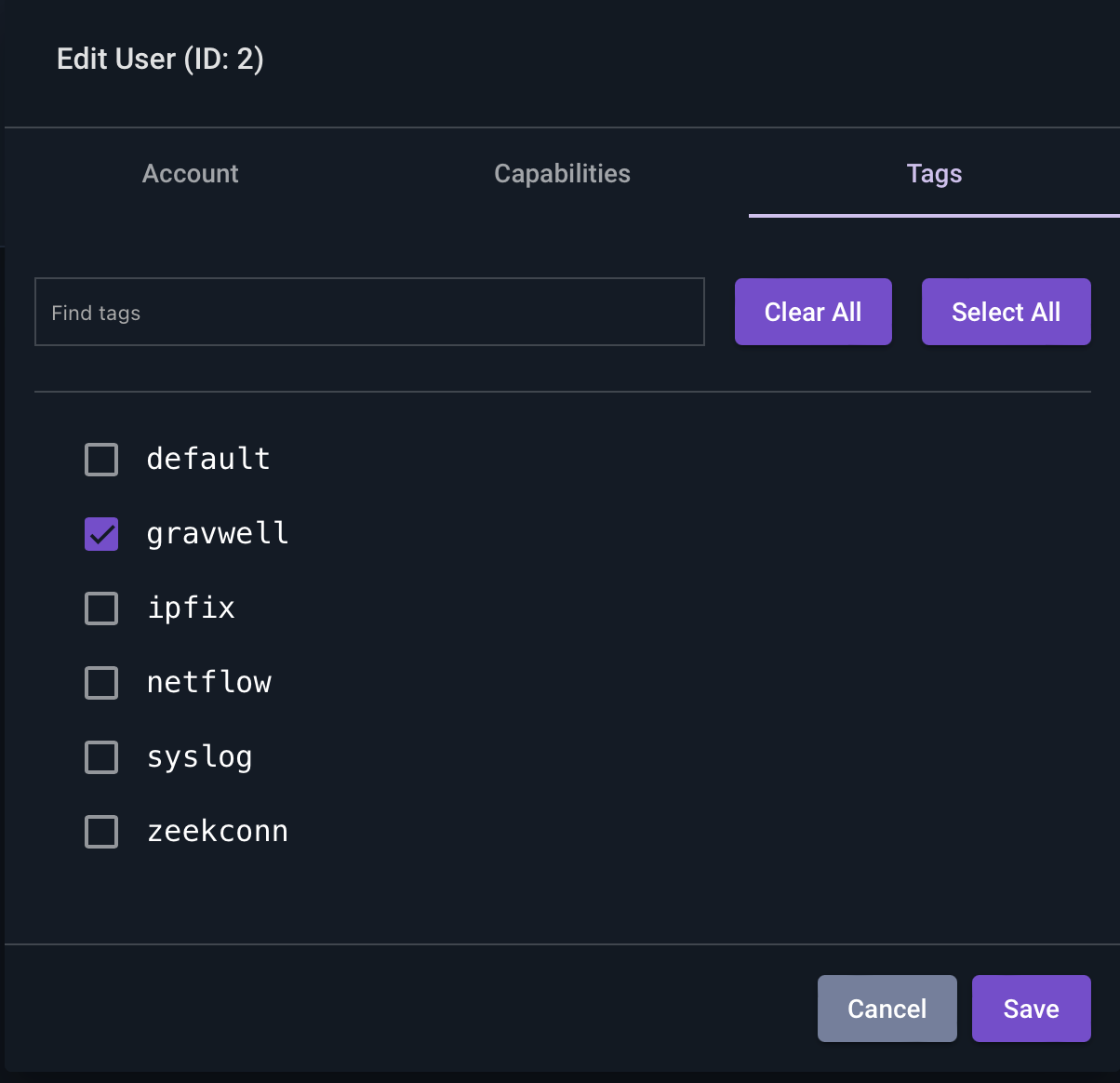
At this point, Kris will have a view like this when he logs in:
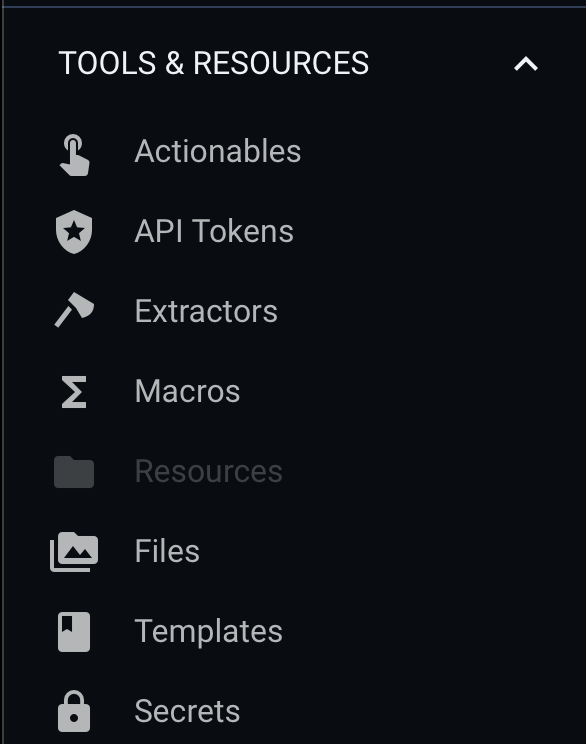
Note the “Resources” menu option is disabled. Kris cannot read from or write to resources, and can’t use them in search either:
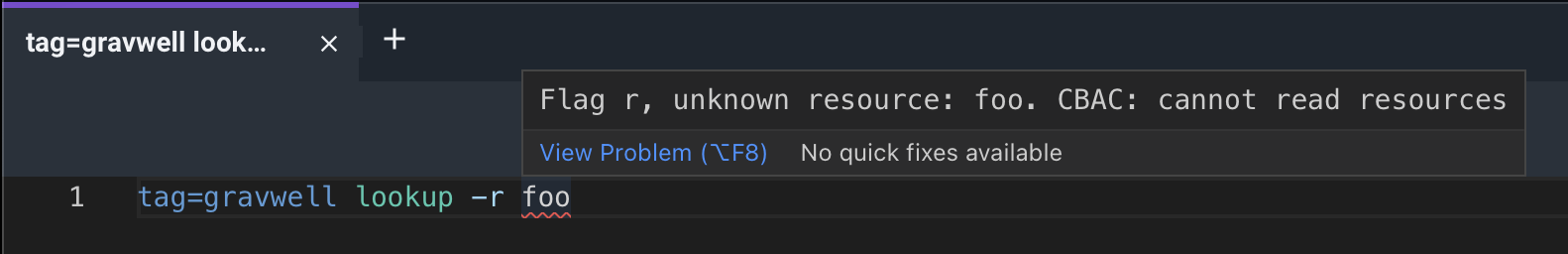
Additionally, when Kris tries to look at what tags are available through autocomplete or the tags menu, he’ll only be able to see the tags we’ve granted him access to.
Groups work in exactly the same way, and any grants a group has will be given to any users in that group.
Conclusion
Well we can all sleep a little better now, knowing that Kris can do a little less thanks to CBAC. If you’re interested in learning more, join our Discord group.
