I'm building a Gravwell Kit for Sysmon! This blog series follows the development of that kit for the awesome (free) sensor for Windows EDR, Sysmon. In this series we'll look at each event type that Sysmon generates to see what data it contains, opportunities for enhancing security, and example queries with Gravwell.
Sysmon is a fantastic Windows tool that was created by By Mark Russinovich and Thomas Garnier as part of the Sysinternals Suite of Windows tools for data collection and analysis. As seen at the sysmon site (sysmon), Microsoft describes sysmon as:
System Monitor (Sysmon) is a Windows system service and device driver that, once installed on a system, remains resident across system reboots to monitor and log system activity to the Windows event log. It provides detailed information about process creations, network connections, and changes to file creation time. By collecting the events it generates using Windows Event Collection or SIEM agents and subsequently analyzing them, you can identify malicious or anomalous activity and understand how intruders and malware operate on your network.
Note that Sysmon does not provide analysis of the events it generates, nor does it attempt to protect or hide itself from attackers. [emphasis mine, but that's why we have Gravwell!]
If you're looking for some background info on Sysmon before proceeding, check out our other posts at gravwell sysmon
Sysmon Event ID #1 - Process Creation
Microsoft provides the description of this event type:
The process creation event provides extended information about a newly created process. The full command line provides context on the process execution. The ProcessGUID field is a unique value for this process across a domain to make event correlation easier. The hash is a full hash of the file with the algorithms in the HashType field.
The key properties present in the process creation event are:
- Computer
- ProcessId
- ProcessGuid
- Image
- OriginalFileName
- Description
- CommandLine
- User
- Hashes
- ParentImage
- ParentProcessId
- ParentCommandLine
We're going to key off of the Computer and Image properties for most of the activity as that tells us which Computer and the full EXE path for the new process being created. Also of note are the Command Line and Parent properties which help identify origination and additional context about the process.
The MITRE ATT&CK framework is a popular way to evaluate coverage of a log source and/or analysis technique. We'll be discussing this framework as it applies to some of these event types, but the process creation is generally self-evident. The additional properties generated by Sysmon, however, do give us some insights into:
The ProcessGuid deserves special mention as important for future use. The other Sysmon events, such as Event ID 22 which logs DNS, will include the process Image (exe path) and the Guid. This is key for correlating and Data Fusion of various Sysmon events. More on that in future posts.
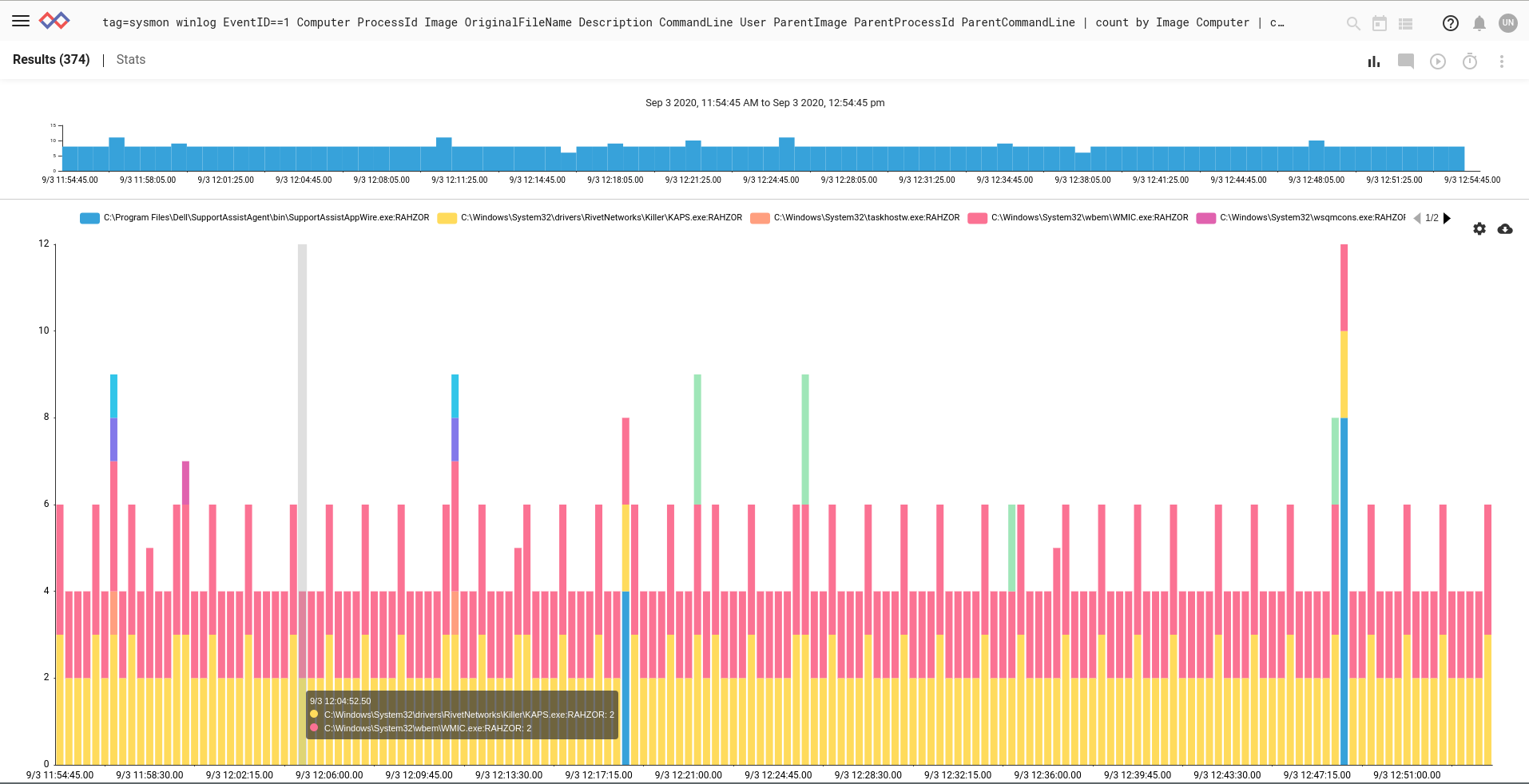
Let's see this in action running on my home office network. I'm going to run a search to chart process creation grouped by EXE and Computer so I can get an idea about how often processes are created and which ones are the most frequent. I was a little taken aback to see two processes dominating the graph:
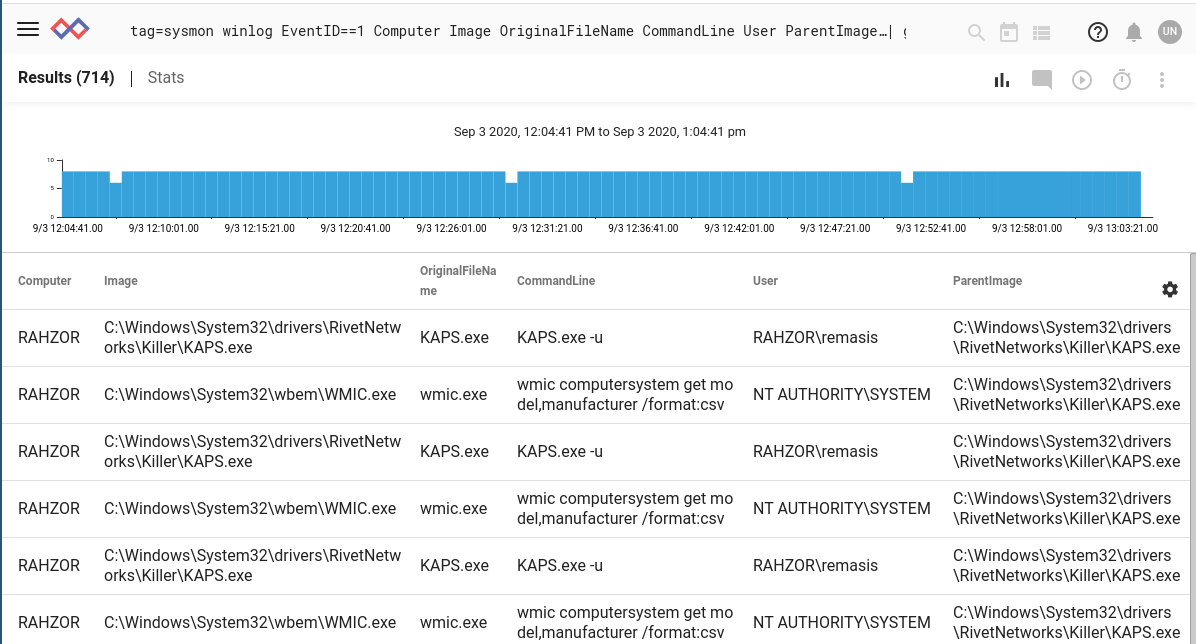
This looks like some shenanigans. A process is executed so often and under potential shady circumstances. First KAPS.exe issues a wmic command `wmic computersystem get model,manufacturer /format:csv` and then launches itself with a "-u" flag. I can guess what the point of this is. Normally I would investigate using another Sysmon ID for network creation, but for this post we'll stick to ID 1.
If you don't have this level of process creation audit capability at your organization, or want to talk shop about what kind of benefits you can get with this kind of data... well we're happy to have those kinds of conversations because that's what we love. Click this button:
Keep reading to get into some more technical nitty gritty.
Let's look at a sample Event:
<?xml version="1.0" encoding="UTF-8"?>
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Microsoft-Windows-Sysmon" Guid="{5770385f-c22a-43e0-bf4c-06f5698ffbd9}" />
<EventID>1</EventID>
<Version>5</Version>
<Level>4</Level>
<Task>1</Task>
<Opcode>0</Opcode>
<Keywords>0x8000000000000000</Keywords>
<TimeCreated SystemTime="2020-07-29T03:53:16.099233400Z" />
<EventRecordID>3319506</EventRecordID>
<Correlation />
<Execution ProcessID="4932" ThreadID="5540" />
<Channel>Microsoft-Windows-Sysmon/Operational</Channel>
<Computer>RAHZOR</Computer>
<Security UserID="S-1-5-18" />
</System>
<EventData>
<Data Name="RuleName" />
<Data Name="UtcTime">2020-07-29 03:53:16.097</Data>
<Data Name="ProcessGuid">{e8a27be9-f2ac-5f20-0000-0010e2d20b02}</Data>
<Data Name="ProcessId">2916</Data>
<Data Name="Image">C:\Windows\System32\wbem\WMIC.exe</Data>
<Data Name="FileVersion">10.0.18362.1 (WinBuild.160101.0800)</Data>
<Data Name="Description">WMI Commandline Utility</Data>
<Data Name="Product">Microsoft® Windows® Operating System</Data>
<Data Name="Company">Microsoft Corporation</Data>
<Data Name="OriginalFileName">wmic.exe</Data>
<Data Name="CommandLine">wmic computersystem get model,manufacturer /format:csv</Data>
<Data Name="CurrentDirectory">C:\Windows\System32\drivers\RivetNetworks\Killer\</Data>
<Data Name="User">NT AUTHORITY\SYSTEM</Data>
<Data Name="LogonGuid">{e8a27be9-b192-5f20-0000-0020e7030000}</Data>
<Data Name="LogonId">0x3e7</Data>
<Data Name="TerminalSessionId">0</Data>
<Data Name="IntegrityLevel">System</Data>
<Data Name="Hashes">MD5=29B7D02A3B5F670B5AF2DAF008810863,SHA256=96BEC668680152DF51EC1DE1D5362C64C2ABA1EDA86F9121F517646F5DEC2B72,IMPHASH=2169BDA7AED3E42F1A59C8141542EC0C</Data>
<Data Name="ParentProcessGuid">{e8a27be9-b194-5f20-0000-0010f39d0600}</Data>
<Data Name="ParentProcessId">7076</Data>
<Data Name="ParentImage">C:\Windows\System32\drivers\RivetNetworks\Killer\KAPS.exe</Data>
<Data Name="ParentCommandLine">"KAPS.exe"</Data>
</EventData>
</Event>
Example Gravwell Queries
Here are some Gravwell queries for interrogating Sysmon data. In building the README playbook for Sysmon within Gravwell, I'm including these queries but I'll be adding them to the Query Library or Templates within Gravwell as part of the actual Kit for publication.
Basic Extraction
tag=sysmon winlog EventID==1 Computer ProcessId Image OriginalFileName Description CommandLine User ParentImage ParentProcessId ParentCommandLine | tableExtract Hashes as well (but don't display them)
tag=sysmon winlog EventID==1 Computer ProcessId Image OriginalFileName Description CommandLine User Hashes ParentImage ParentProcessId ParentCommandLine
| kv -e Hashes -d "," MD5 SHA256
| table Computer Image OriginalFileName Description CommandLine User ParentImage ParentProcessId ParentCommandLine
Common Processes table
tag=sysmon winlog EventID==1 Computer ProcessId Image OriginalFileName Description CommandLine User ParentImage ParentProcessId ParentCommandLine
| count by Image Computer User
| table Image Computer User count
Uncommon Processes table
tag=sysmon winlog EventID==1 Computer ProcessId Image OriginalFileName Description CommandLine User ParentImage ParentProcessId ParentCommandLine
| count by Image Computer User
| sort by count asc
| table Image Computer User countTop Process Spawners
tag=sysmon winlog EventID==1 Computer ProcessId Image OriginalFileName Description CommandLine User ParentImage ParentProcessId ParentCommandLine
| count by Image ParentImage
| stats sum(count) by ParentImage
| table ParentImage countSearch for a specific exe
tag=sysmon winlog EventID==1 Computer ProcessId Image OriginalFileName Description CommandLine User ParentImage ParentProcessId ParentCommandLine
| grep -e Image -i "kaps"
| tableConclusion
Sysmon is awesome. Gravwell is awesome. Data is better together.
Look for our upcoming announcements on Gravwell Big Bang and additional Kits as we develop and release them. We're excited about how Kits allow people to go from Sysmon zero to Sysmon Hero in no time flat.
Interested in adding Gravwell+Sysmon data to your Operations and Security arsenal? Request a Free Trial, or click this big ol' red button and we'd be happy to chat about how that might fit into your organization.