We're building a Gravwell Kit for Sysmon! This blog series examines some of the event types that Sysmon generates to see what data they contain, opportunities for enhancing security, and example queries with Gravwell. Part 1 covered the Process Creation event type. In part 2 we jump into: Network Connection events!
Sysmon is a powerful Windows tool created by Mark Russinovich and Thomas Garnier as part of the Sysinternals Suite of Windows tools for analysis and data collection. According to Microsoft's description, Sysmon does not provide analysis of the events it generates, nor does it attempt to protect or hide itself from attackers (emphasis mine, but that's where Gravwell comes in!).
For some background information on Sysmon, visit Sysmon v15.14 or check out our previous blog posts at Sysmon By Gravwell
Sysmon Event ID #3 - Network connection
The Sysmon network connection event logs TCP/UDP connections on a machine, and is disabled by default. A configuration file is required to enable the data source, and each connection is linked to a process through the ProcessId and ProcessGUID fields. The network connection event also contains the source and destination host names IP addresses, port numbers and IPv6 status.
SwiftOnSecurity configuration file does some filtering here to exclude files located in standard Windows directory. If you do not want this and would rather "ingest everything" and let the power of Gravwell search help, you should remove this filtering from your Sysmon configuration files. Tay offers this comment: "By default this configuration takes a very conservative approach to network logging, limited to only extremely high-signal events."
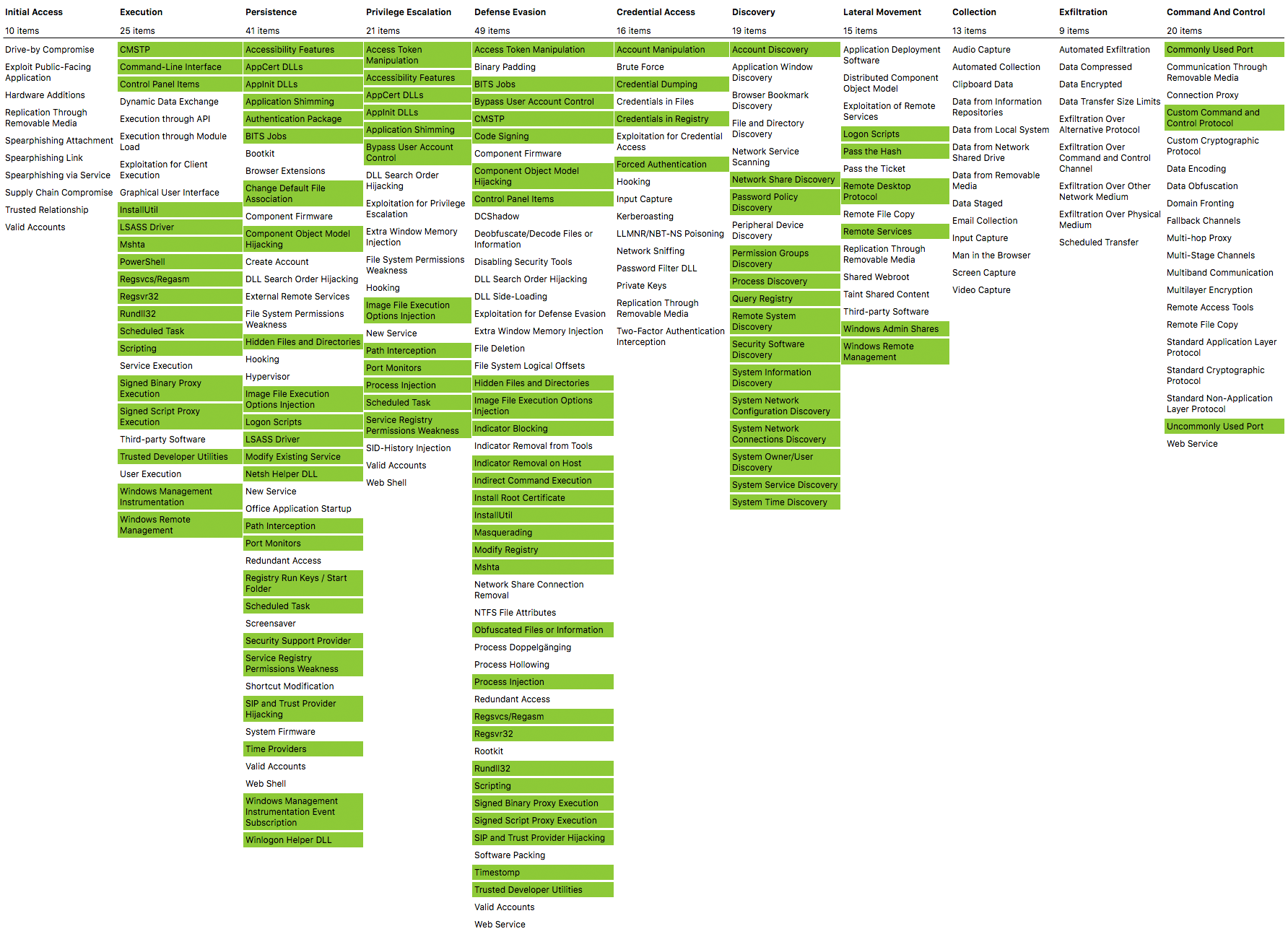
An additional configuration that's incredibly helpful is created and maintained by Olaf Hartong and published here. Olaf and contributors have put a lot of work into mapping Sysmon detectable events to the MITRE ATT&CK framework. With sysmon, his config, and Gravwell for collection and search of those events, you can expect this kind of coverage over your Windows activity!
The key properties present in the network connection event are:
- Computer
- Image
- SourceIp
- SourceHostname
- SourcePort
- DestinationIp
- DestinationHostname
- DestinationPort
We're going to key off of the Computer, Image, and standard 4tuple network properties for most of the activity. Also of note are the Hostname properties, but they aren't always present.
The MITRE ATT&CK framework is a popular way to evaluate coverage of a log source and/or analysis technique. Network traffic and the associated exe's originating said traffic can give us coverage of some of the TTPs present in the framework. The most notable are:
Here are some example insights I can pull out using Event ID 3. For these examples, I'm using SwiftOnsecurity's config, so they are pretty much relegated to binaries located in nonstandard, userspace, or unusual locations. This config doesn't log each and every connection.
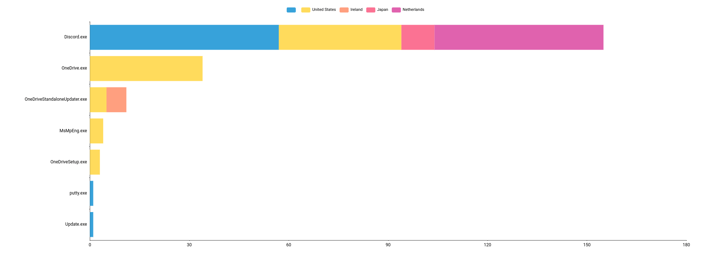
A common visualization for network data is looking at a breakdown of where destination traffic is headed, geographically speaking. With Sysmon, we can even break this down to the process level.
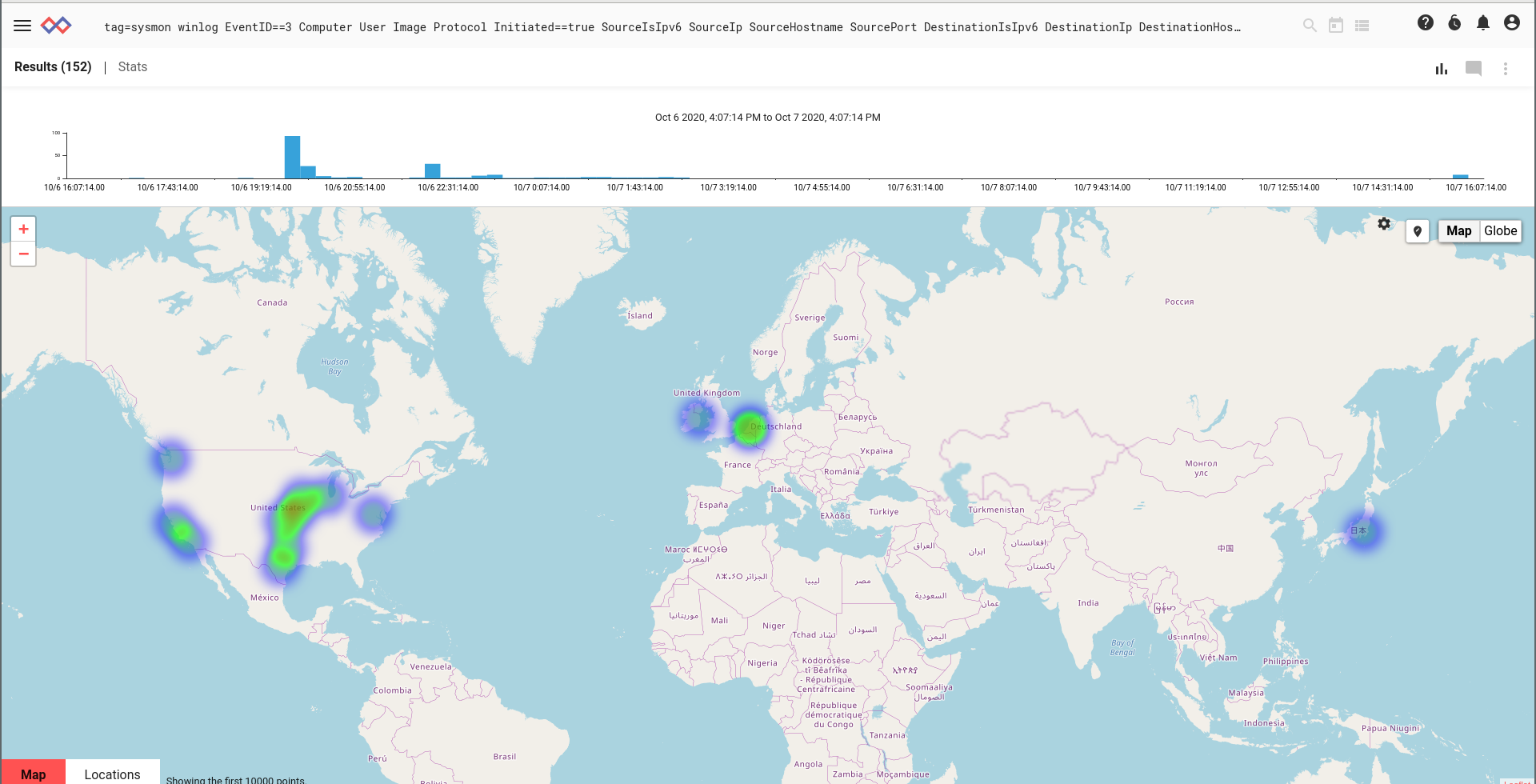
With the power of the Gravwell query pipeline, we can easily change this search to give us a map display of the same information for easy human pattern recognition.
Let's examine a sample Event:
<?xml version="1.0" encoding="UTF-8"?>
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Microsoft-Windows-Sysmon" Guid="{5770385f-c22a-43e0-bf4c-06f5698ffbd9}" />
<EventID>3</EventID>
<Version>5</Version>
<Level>4</Level>
<Task>3</Task>
<Opcode>0</Opcode>
<Keywords>0x8000000000000000</Keywords>
<TimeCreated SystemTime="2020-07-29T23:20:42.210216500Z" />
<EventRecordID>179603</EventRecordID>
<Correlation />
<Execution ProcessID="3276" ThreadID="4056" />
<Channel>Microsoft-Windows-Sysmon/Operational</Channel>
<Computer>BEBOP</Computer>
<Security UserID="S-1-5-18" />
</System>
<EventData>
<Data Name="RuleName">Usermode</Data>
<Data Name="UtcTime">2020-07-29 23:20:33.560</Data>
<Data Name="ProcessGuid">{8fe600b4-0447-5f22-0000-0010a1da740f}</Data>
<Data Name="ProcessId">9580</Data>
<Data Name="Image">C:\Users\grav\AppData\Local\Microsoft\OneDrive\OneDriveStandaloneUpdater.exe</Data>
<Data Name="User">BEBOP\grav</Data>
<Data Name="Protocol">tcp</Data>
<Data Name="Initiated">true</Data>
<Data Name="SourceIsIpv6">false</Data>
<Data Name="SourceIp">10.18.12.2</Data>
<Data Name="SourceHostname">BEBOP</Data>
<Data Name="SourcePort">60921</Data>
<Data Name="SourcePortName" />
<Data Name="DestinationIsIpv6">false</Data>
<Data Name="DestinationIp">52.114.158.91</Data>
<Data Name="DestinationHostname" />
<Data Name="DestinationPort">443</Data>
<Data Name="DestinationPortName">https</Data>
</EventData>
</Event>
Interrogate Sysmon Data with Gravwell Queries
I'll be adding these queries to the Query Library or Templates as part of our Sysmon Kit (launching soon!), and am also building the README playbook for Sysmon within the current Gravwell platform.
Basic Extraction
tag=sysmon winlog EventID==3 Computer User Image Protocol Initiated SourceIsIpv6 SourceIp SourceHostname SourcePort DestinationIsIpv6 DestinationIp DestinationHostname DestinationPort
| table
Top Countries
tag=sysmon winlog EventID==3 Computer User Image Protocol Initiated==true SourceIsIpv6 SourceIp SourceHostname SourcePort DestinationIsIpv6 DestinationIp DestinationHostname DestinationPort
| geoip DestinationIp.CountryName
| count by Image CountryName
| table Image CountryName count
tag=sysmon winlog EventID==3 Computer User Image Protocol Initiated==true SourceIsIpv6 SourceIp SourceHostname SourcePort DestinationIsIpv6 DestinationIp DestinationHostname DestinationPort
| geoip DestinationIp.Location
| pointmap Image
tag=sysmon winlog EventID==3 Computer User Image Protocol Initiated==true SourceIsIpv6 SourceIp SourceHostname SourcePort DestinationIsIpv6 DestinationIp DestinationHostname DestinationPort
| geoip DestinationIp.Location
| heatmap
In Summary
Data is better together. There's a special kind of magic that happens when you can fuse together multiple unstructured data sources like sysmon, DNS, netflow, binary, and time series data (among a multitude of others that Gravwell can ingest natively). Combining the information gathered from disparate data sources allows you to supercharge your threat hunt, or sculpt with your data in new and exciting ways and get to the ground truth in your operations.
Sysmon is awesome, and our soon-to-launch Sysmon Kit will make it even easier for you to get up and running quickly with this powerful data source.
Interested in adding Gravwell+Sysmon data to your arsenal? Request a Free Trial, or click the big red button below and one of our Gravwell Guides will happily give you a tour of our data fusion platform.