by
Gravwell
|
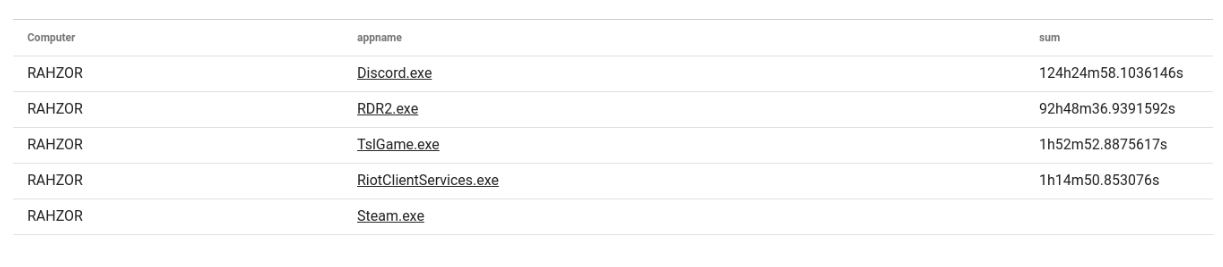
This week's Query of the Week uses Sysmon logs to see when applications access the microphone, then displays a table for each.
tag=sysmon winlog Provider=="Microsoft-Windows-Sysmon" EventID==13 TargetObject RuleName~"Audio Capture" Computer TimeCreated Details | sort by time asc | regex -e Details "\((?P<qword>.+)\)" qword != "0x00000000-0x00000000" | regex -e TargetObject "#(?P<appname>[^#]+)\\LastUsedTime(?P<mic_action>\S+)" | diff TIMESTAMP by Computer appname | eval mic_action=="Stop" | stats count as Count sum(diff) as TotalTime by Computer appname | table Computer TotalTime Count
Example table that could result from the query:
Visit gravwell.io/query to view an archive of our previous Query of the Week posts.